Understanding Cross-Site Request Forgery (CSRF) and staying safe
CSRF exploits the trust between a user's browser and a website to perform unauthorized actions, learn about ways to stay safe.

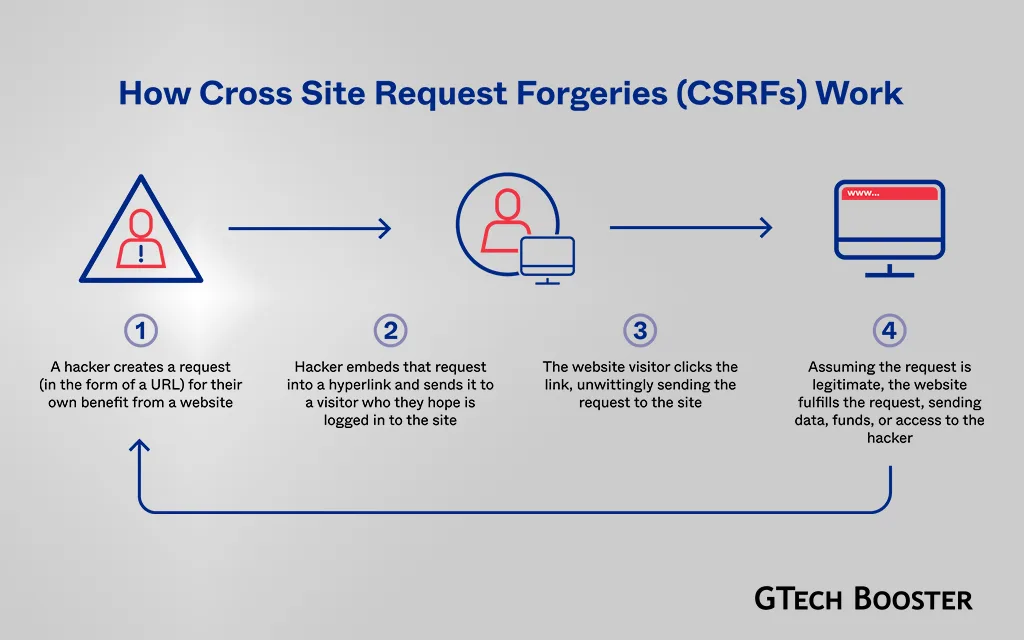
Cross-Site Request Forgery (CSRF) is a type of malicious exploit in web security where unauthorized commands are submitted from a user that a web application trusts. In a CSRF attack, an innocent user is tricked by an attacker into unknowingly submitting a web request that they did not intend. This can lead to actions being performed on the website without the user’s consent, potentially causing data leakage, changes in session state, or manipulation of the user’s account.
The attack exploits the trust that a website has in a user’s browser, rather than the trust a user has for a particular site as in Cross-Site Scripting (XSS). Attackers can trick users into performing actions like unauthorized fund transfers, changing passwords, or making unauthorized purchases. CSRF attacks can be mitigated by using techniques like Anti-CSRF tokens, which involve creating and comparing randomly generated token strings to prevent attackers from successfully executing attacks without an unlikely guess.
These tokens are embedded into forms on websites, and when a user submits the form, the token is returned and checked by the server to ensure its validity, thus preventing unauthorized actions. CSRF attacks can have severe consequences, including data theft, unauthorized access to accounts, and complete compromise of a web application, especially if the victim has administrative privileges within the system.
CSRF (Cross-Site Request Forgery) protection
CSRF (Cross-Site Request Forgery) protection is a security measure that prevents unauthorized requests from being sent on behalf of a user. It is used to protect websites from various attacks, such as session hijacking and account tampering. Here are some common methods and best practices for implementing CSRF protection:
Synchronizer Token Pattern (STP)
This is a popular and recommended method for mitigating CSRF attacks. In STP, the server sends a token associated with the current user’s identity to the client. The client then sends back the token to the server for verification. If the server receives a token that doesn’t match the authenticated user’s identity, the request is rejected.
Anti-forgery tokens
These tokens can be used with any authentication protocol where the browser silently sends cookies. They help prevent CSRF attacks by ensuring that only authorized requests can be processed.
Custom headers
In some cases, you can use custom headers to add CSRF protection to your API endpoints. For example, the client app can append a custom header to requests that require CSRF protection, and the API checks for the existence of this header before processing the request.
Built-in or existing CSRF implementations
Some frameworks and libraries have built-in CSRF protection, such as ASP.NET’s built-in protection for .NET. It is essential to research and understand the CSRF mitigation techniques provided by the technologies you are using before implementing them.
Remember that no security measure is foolproof, and as such it is essential to stay up-to-date with the latest security best practices and recommendations.














