Data Protection
Looking into the SSL port

Ghana’s One Million Coders Program: Empowering a Digital Future

These Military Grade data storage protection from iStorage can save you from spill

Understanding Ransomware and what make it daring

How To Setup the Kingston IronKey™ Vault Privacy 50 Encrypted USB Flash Drive

10 easy steps to Recover Data from a Corrupt SD Card

Samsung Security Tech Forum 2021

Privacy options on the internet: Apple-Facebook

EU ethics Guidelines For Trustworthy AI: Chapter 1

Proposed EU Copyright Directive Approved – Without Amendments

4 ways hackers can hack you right now

Threat Modeling, a beginners guide

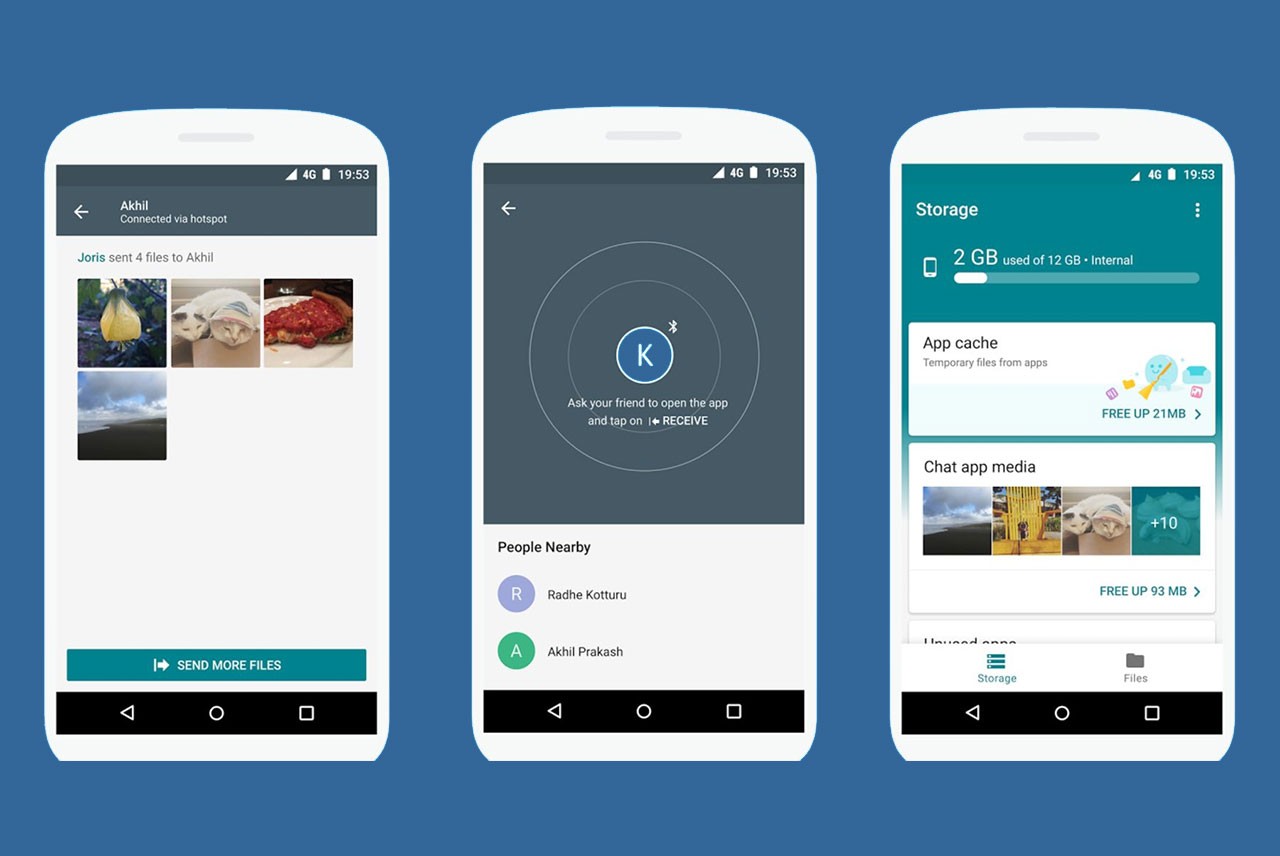
How to Keep up with storage capacity with Files Go
GDPR: Need to know

Know this: Don't Brick your Smartphone

Data Protection Acts I




